🚨Monday quick tip that will save you hours of troubleshooting. Thanks to Yuri Gasparini for the gem. 🙏🏻
💻 Scenario
You want to authenticate a device via certificate (EAP-TLS), using Intune Cloud PKI, SCEP profiles via Intune, and the server is a Windows NPS server. Clients are domain-joined, Hybrid Entra Joined, and managed by Intune.
🔨 Configuration
The SCEP certificate, in this case, has specific requirements, especially for the Subject Alternative Name (SAN). You can find all the details here:
📃 Certificate requirements when you use EAP-TLS or PEAP with EAP-TLS
⚠️ Attention: here’s the key tip
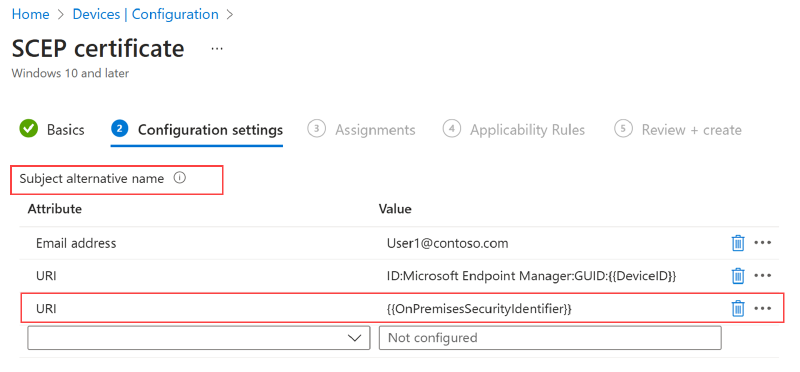
But the real key tip is this. Beyond the usual parameters to configure in the SCEP profile on Intune, it’s crucial in this scenario to correctly populate the SAN with the computer account’s UPN. Too bad there isn’t a dedicated, ready-to-use variable. How can you do it?
By using a mixed combination of variables and static text, like this:
1️⃣ User Principal Name (UPN) ➡️ {{DeviceName}}@domainname.local
And don’t forget strong mapping!
2️⃣ URI ➡️ {{OnPremisesSecurityIdentifier}}
For further insights into SCEP profiles:
📃 Create and assign SCEP certificate profiles in Intune
📃 KB5014754: Certificate-based authentication changes on Windows domain controllers
Your IT Specialist,
Riccardo